Provisioning Configuration
First some background.
For every new HyDip organization created there is a set of predefined system groups which can be used for easier user management and access control.
You can find the default system groups by logging into your HyDip dashboard.
- Click on the settings button
- Select 'Organisation’ tab.
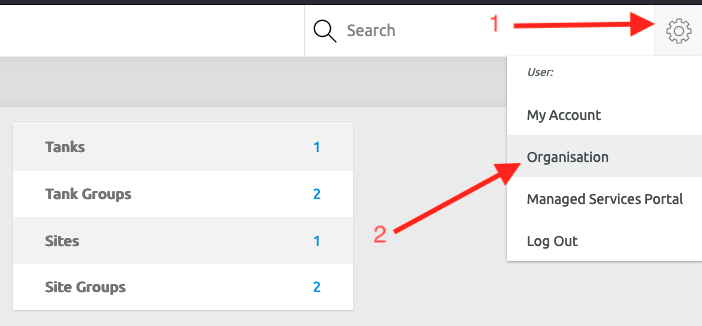
- Select ‘Users/groups’ tab on left-hand-side menu.
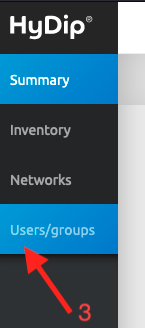
- Now you should see all the system groups defined for your organization.
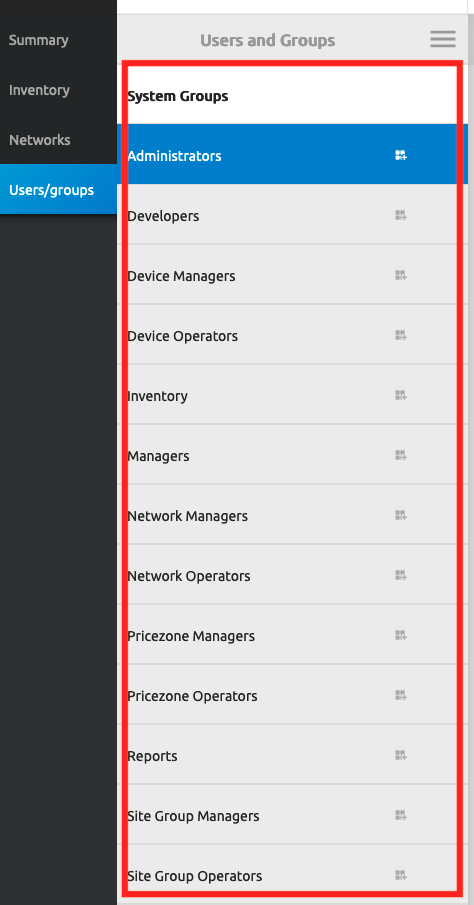
We can link those system groups to Azure AD groups for easier members management and permission granting.
Now we need to install HyDip Provisioning application. Learn more on how to install Enterprise Application by reading the following documentation https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/add-application-portal.
Once the HyDip Provisioning application is installed we need to configure it for communication with HyDip servers.
To do this:
- Go to the app’s Provisioning section.
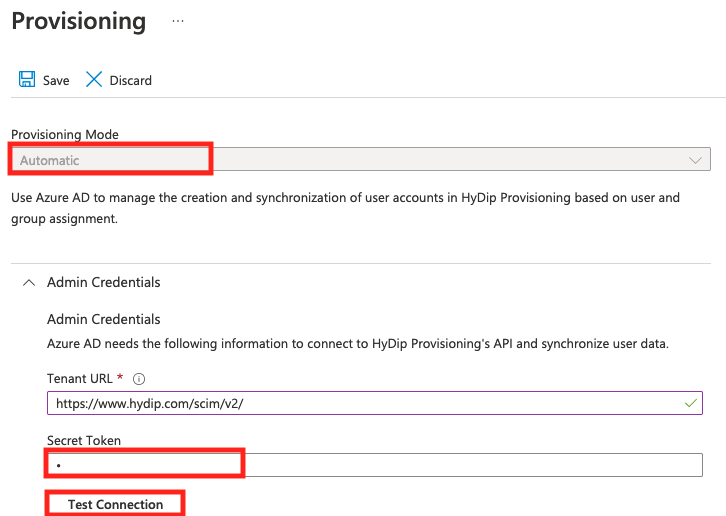
- In the provisioning properties:
- Set the Provisioning Mode to Automatic
- Use token generated in step 4. of the SSO Configuration Steps and use that value to configure Secret Token.
- Click Test Connection. Everything should be running smoothly, and the test should finish with success.
- Click Save. - All that is left to do is define users & groups that will be allowed to synchronize with HyDip services.
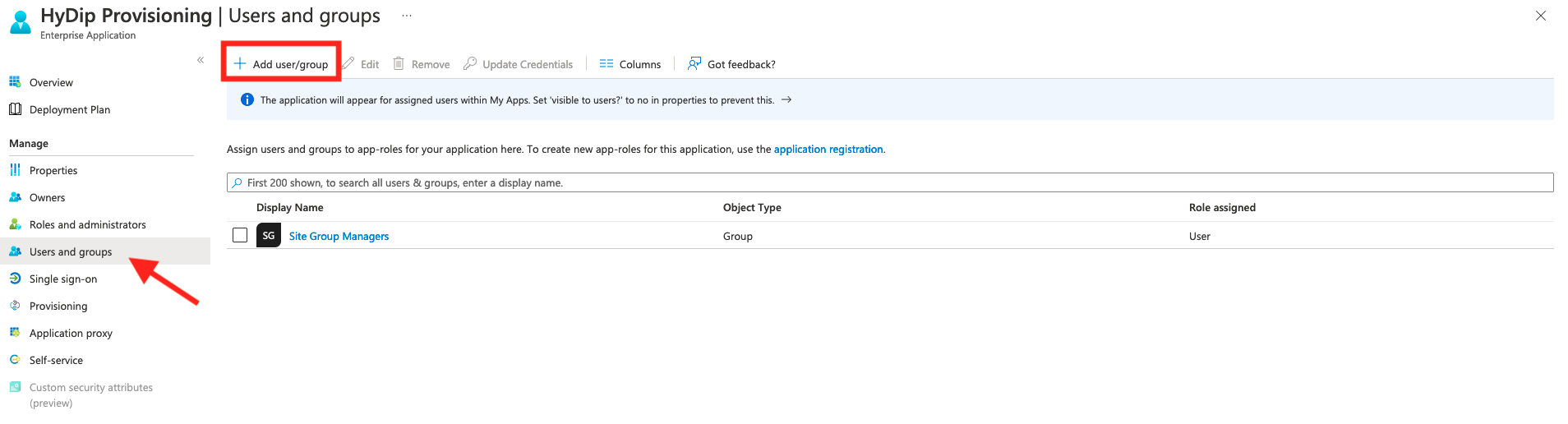
Create a user group with a name corresponding to the name of system groups you discovered in step 4 of SSO Configuration. Then add members to those groups. Members whose e-mail addresses are not registered with HyDip platform will get created. If a member with corresponding e-mail address exists on our servers, it will get linked to the Azure AD resource and all the changes you make in Azure AD will be mirrored in our platform.
To learn more on how to create groups and add members you can read here https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-groups-create-azure-portal.
Remember that AD does not support syncing users withing nested groups.
Updated 8 months ago
